2023.1 Release Notes
New Features and Enhancements that are available in Germain UX 2023.1 release.
COMPLIANCE
SOC 2 / Type 1 Audit
Customers: American Airlines, eBay, Ease, Online Stock Platform
Description
Last month, we accomplished the following milestones:
Successfully completed the Soc2/Type1 Audit, including attestation. Detailed information is enclosed regarding the audit findings and outcomes.
Commenced a 12-month Soc2/Type2 audit process, which will further evaluate and assess our compliance over an extended period.
These achievements demonstrate our commitment to maintaining and enhancing our security practices and compliance standards.

MONITORING AND ANALYTICS FEATURES
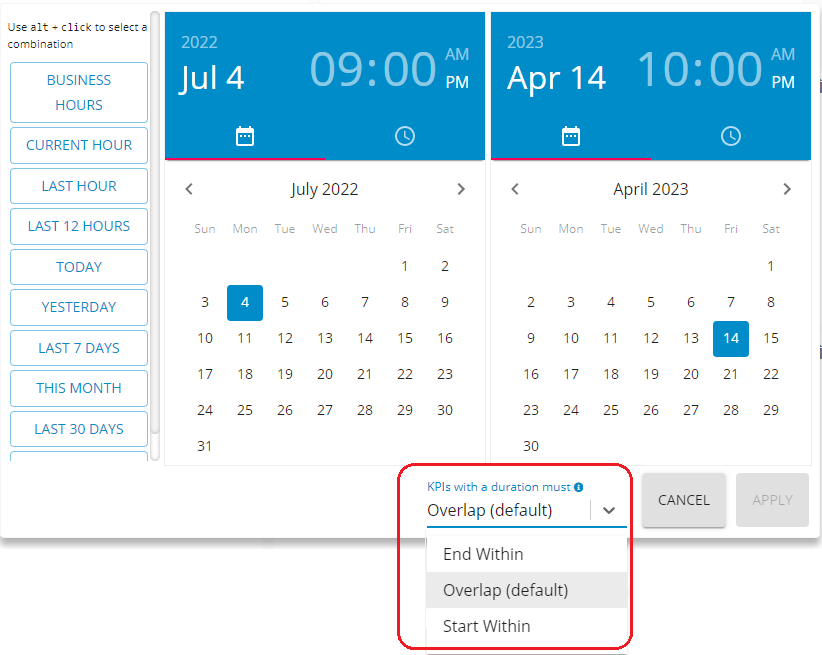
[End within], [Overlap] or [Start Within] in Date/Time range
Customers: Ease
Description
The platform offers the ability to display metrics for Key Performance Indicators (KPIs) based on their duration. This includes options to filter metrics based on whether the KPI's duration [ends within], [overlaps], or [starts within] a specified datetime range.
KPIs for Business, IT, Marketing, UX and Web Ops
Customers: All
Description
The following are preconfigured Key Performance Indicators (KPIs) available in Germain UX:
KPIs/Pivots/Measures for Business Ops.
KPIs/Pivots/Measures for IT Ops.
KPIs/Pivots/Measures for Marketing Ops.
KPIs/Pivots/Measures for UX Ops.
KPIs/Pivots/Measures for Web Administrators.
Measures for [User Session Replay] KPI
Customers: General Electric, SPB Insurance
Description
Several new measures have been added to the [User Session Replay] and [User Click] Key Performance Indicators (KPIs).
The following are the new measures for the [User Session Replay] and [User Click] KPIs:
Count of New Users vs Returning users
Top visited pages (volume per page)
Mobile vs Desktop users (volume, performance)
Top landing pages
Top exit pages
Top references
Top campaigns
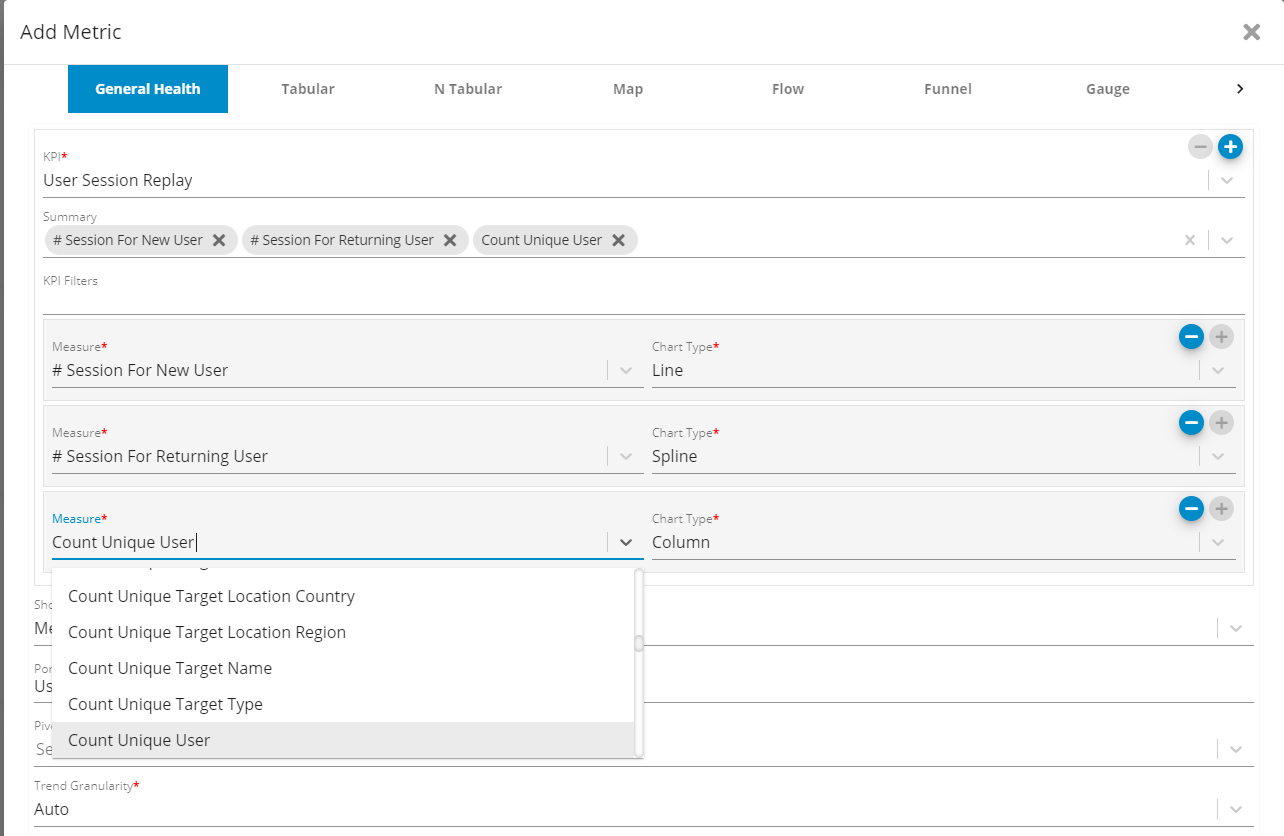
More details about all other measures for Session Replay.
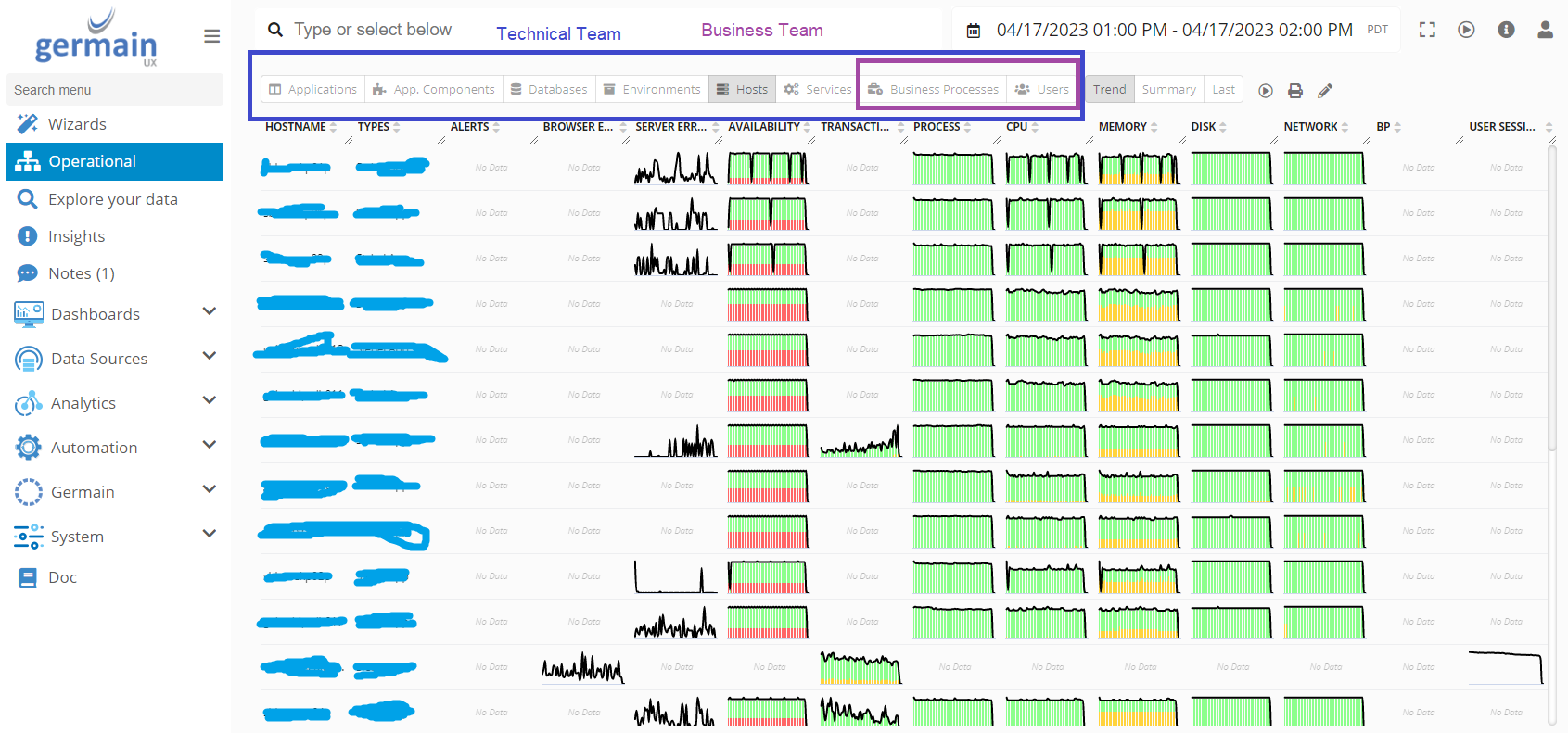
Operational Dashboard’s Tab Visibility
Customers: A Large Online Trading Platform (we cannot disclose its name)
Description
The visibility of tabs in the Operational Dashboard is determined by the Team Type, either Business or Technical.
The Business Team has visibility to the following tabs: [Business Process] and [Users].
The Technical Team has visibility to all tabs, including: [Application], [App Components], [Databases], [Environments], [Hosts], [Services], [Business Process], and [Users].
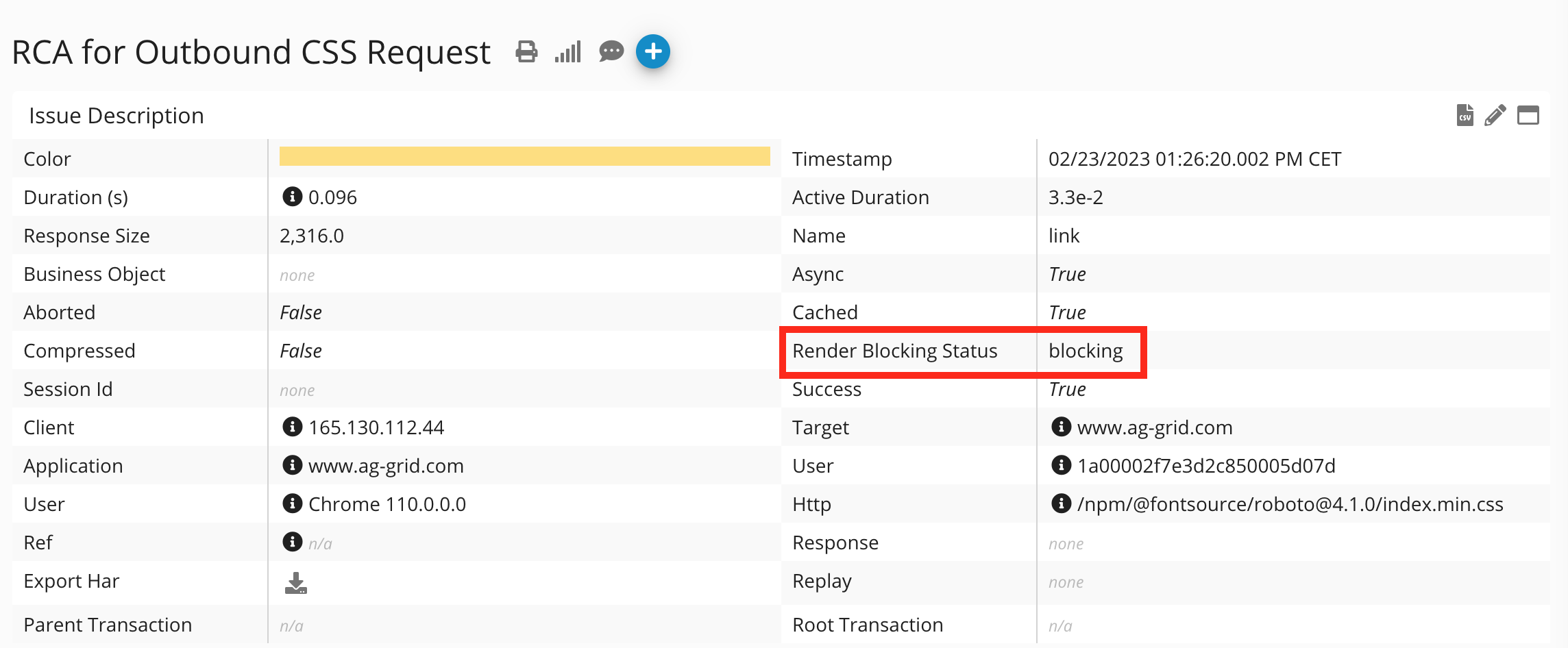
Render Blocking Status of a HTTP Request
Customers: A Large Online Trading Platform (we cannot disclose its name)
Description
Render-blocking resources refer to static files such as fonts, CSS, and JavaScript that can hinder or delay the browser from rendering page content promptly. The Render-blocking Status is now accessible through various Germain Key Performance Indicators (KPIs), such as the Outbound CSS Request KPI.
More details about renderBlockingStatus: https://developer.mozilla.org/en-US/docs/Web/API/PerformanceResourceTiming/renderBlockingStatus
Example
SALESFORCE.COM - More KPIs
Customers: Largest US-Based Healthcare
Description
Additional Key Performance Indicators (KPIs), portlets, and dashboards have been added to specifically monitor and provide insights on Salesforce performance.
GERMAIN UX KPIs FOR SALESFORCE.COM MONITORING AND INSIGHTS |
Salesforce Apex Class |
Salesforce Apex Code Coverage |
Salesforce Apex Custom Action |
Salesforce Apex Trigger |
Salesforce Api Event |
Salesforce Browser Performance Count |
Salesforce Bulk Api Result Event |
Salesforce Classic Record Event |
salesforce Code Debug Event |
Salesforce Code Exception |
salesforce Code Execution |
Salesforce Concurrent Long-running Apex Error Event |
Salesforce Credential Stuffing Event |
Salesforce Cron Job |
Salesforce External Service Custom Action |
Salesforce Flow Coverage |
Salesforce Flow Custom Action |
Salesforce Flow Interview |
Salesforce Health Check |
Salesforce Instance Status |
Salesforce Lightning List View Event |
Salesforce Lightning Record Event |
Salesforce Lightning User |
Salesforce List View |
Salesforce Log Generic Event |
Salesforce Login As Event |
Salesforce Login Event |
Salesforce Logout Event |
Salesforce Outbound HTTP Request |
Salesforce Page Performance Count |
Salesforce Platform Event Usage Metric |
Salesforce Process Approval |
Salesforce Process Rule |
Salesforce Record Change Event |
Salesforce Records Count |
Salesforce Report Anomaly Event |
Salesforce Report Execution Event |
Salesforce Resource Usage |
Salesforce Session Hijacking Event |
Salesforce Setup Audit |
Salesforce UI Switch |
Salesforce User Click |
Other Germain UX’s alerts, insights and automation for Salesforce (Classic, Lightning, etc) and for Salesforce Experience Cloud.
MAINTENANCE FEATURES
Data Security Dynamically Enforced at Team level
Customers: A Large Online Trading Platform (we cannot disclose its name)
Description
Data security is dynamically set the Team level depending on the type of “business data” that is being used/processed/accessed by the monitored users/on the monitored application. This is all customizable.
Here's how it works:
Each Team is assigned a unique accessId when it is created. These accessIds are visible on the Teams view. For example, the 'Business Team' may have accessId 't1', while the 'Development Team' may have accessId 't2'.
Data can be annotated with an expression that determines which teams have access to it. This is achieved by setting the 'access' field.
For instance, a UxSession with access 't1 || t2' would be visible to members of the Business Team (t1) or the Development Team (t2) who have access to view the data.
If the access field is not set, anyone with permission to view data will be able to see the fact.
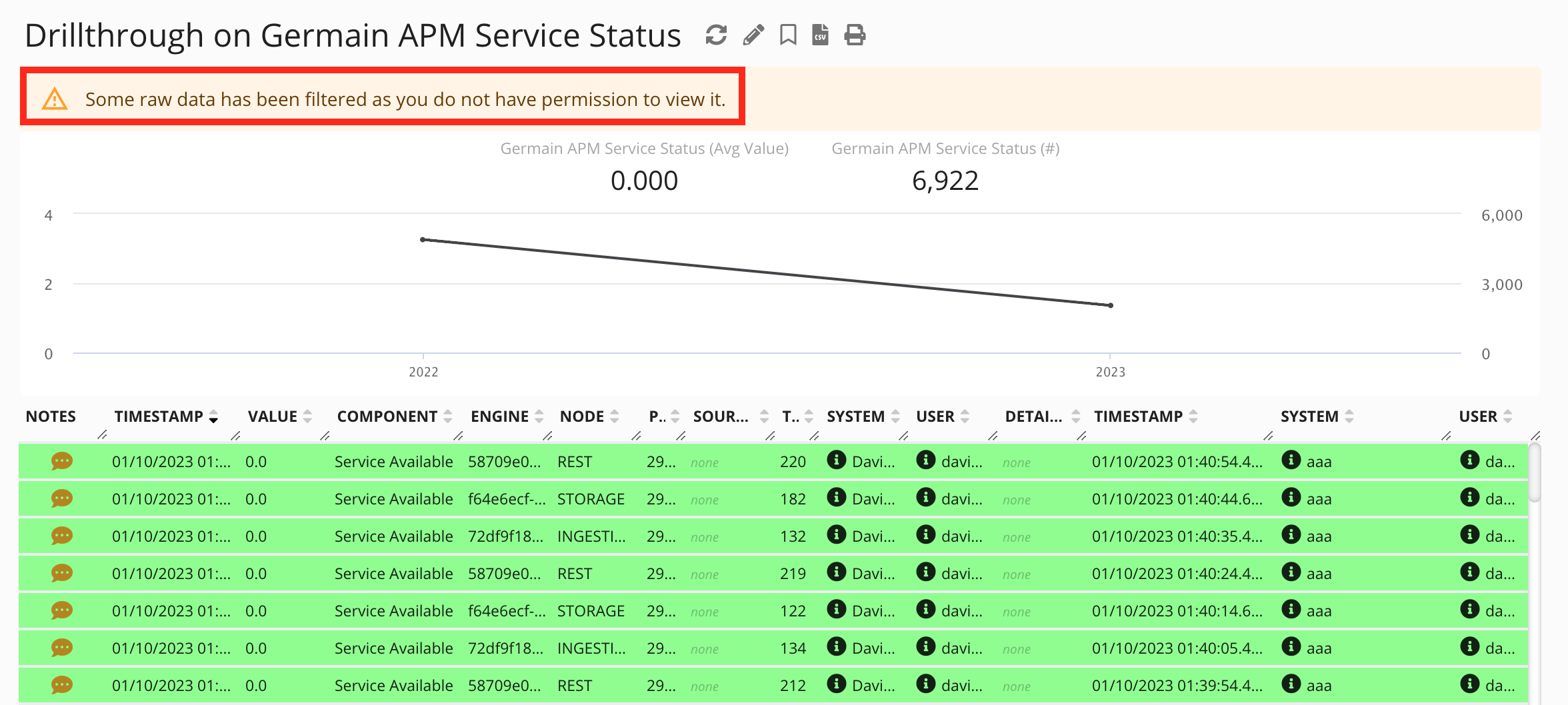
When a user attempts to access an RCA (Root Cause Analysis) for a fact they don't have access to, the data should not be visible to them. Similarly, the Drill-through feature and any RAW data exports should only display data that the user has access to.
Please note that this access control mechanism only affects RAW data. Filtered data is still shown in AGGREGATE data. For example, the count displayed in the Drill-through summary portlet includes data that the user may not have access to. However, we provide a message on the Drill-through indicating if any data is filtered due to access controls
OAuth - Custom Role Mapping
Customers: A Large Online Trading Platform (we cannot disclose its name)
Description
Germain now supports the execution of a custom function to extract Roles from an authenticated OAuth user, similar to how it supports LDAP.
There are a few differences in Role Mapping between LDAP and OAuth:
In LDAP, only Groups and Roles are mapped. However, in OAuth, there are several entities that can be mapped to Roles, based on the OAuth provider and the requested scopes.
Previously, when a user logged in via OAuth, they had to have the AuthenticationConfig.mapRolesFromDBUser configuration setting set to true and have a corresponding user in Germain DB. Alternatively, if AuthenticationConfig.createMissingDBUser was set to true, a DB user would be automatically created. These settings were necessary to obtain any roles because the default mapping from OAuth to GrantedAuthorities only considered the OAuth scopes.
With this enhancement, a custom function can now be executed to extract Roles from an authenticated OAuth user, providing more flexibility in Role Mapping for OAuth users.
Configuration
Details on how to configure OAuth User Management.
Security and Vulnerabilities Fixes
Customers: All customers are required to update Germain with the below patches
Description
As part of our SOC2 compliance program, here are the security breaches that have been found in 2023.1, and patches to address those in 2023.1 or older versions. Please contact us whenever needed..
Vulnerability | Severity | Scope | Detected | Reviewed | Resolved | Affected versions | Fix implemented in | Link |
|---|---|---|---|---|---|---|---|---|
HIGH | yauaa [7.9.0] -> [7.16.0] | 3/18/2023 | 3/20/2023 | 3/20/2023 | <= 2023.1 | 2023.1-14 | ||
HIGH | json-smart [2.4.7] -> [2.4.10] | 3/18/2023 | 3/20/2023 | 3/20/2023 | <= 2023.1 | 2023.1-14 | ||
| HIGH | alpine [3.17.0] => [3.17.2] | 3/18/2023 | 3/20/2023 | 3/20/2023 | <= 2023.1 | 2022.3-61, 2022.4-51, 2022.5-48, 2023.1-14 |
|
Download
