Maintenance - Log4j Vulnerability
Germain team became aware of a widespread security vulnerability commonly known as “Log4j” (CVE-2021-44228, aka. Log4Shell). We have not identified any exposure of any client data as a result of this vulnerability, for both on-premise and cloud users of Germain. However, we do recommend Customers that use Germain onPremise to update their Germain environment as following. Similar configuration was applied to the Germain cloud instances and instances were brought back online today Monday 12/13/21 at 8:35am PST, after completion of our security review.
Pass the following argument: ‐Dlog4j2.formatMsgNoLookups=true to the following services:
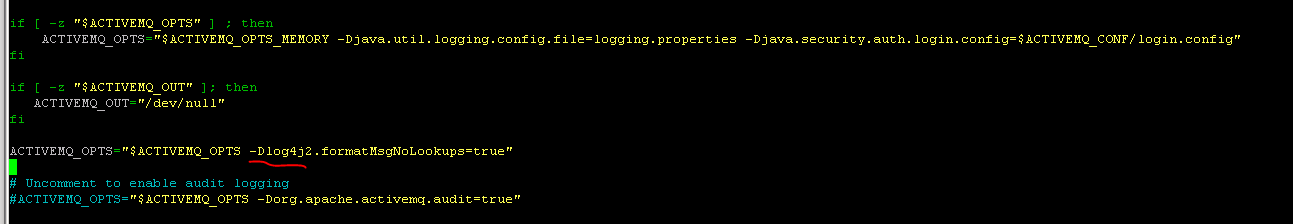
ActiveMQ
Add the parameter to the ACTIVEMQ_OPTS variable (Found under activemq/bin/env):
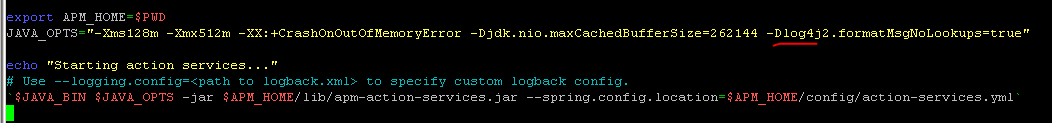
Backend services (action, aggregation, analytics, rtm, session tracking, storage)
Add the parameter to each of the services startup scripts JAVA_OPTS (found under Germain Service directory /bin).
Example:
ElasticSearch
ElasticSearch 7.16.1 or above: https://www.elastic.co/guide/en/elasticsearch/reference/7.16/release-notes-7.16.1.htmlSolr
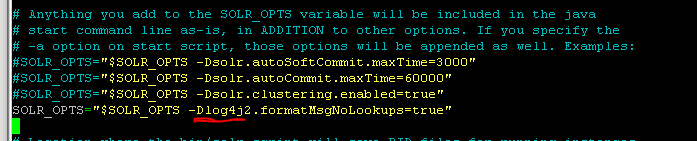
Add the parameter to the SOLR_OPTS variable (Found under Solr directory bin/solr.in.sh):
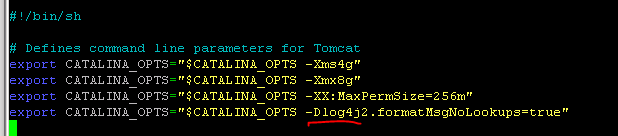
Tomcat
Add the parameter to the CATALINA_OPTS variable for each Tomcat instance (Found under Tomcat instance dir /bin/setenv.sh):
More technical details can be found here: https://www.lunasec.io/docs/blog/log4j-zero-day
